Authorization
V8.0
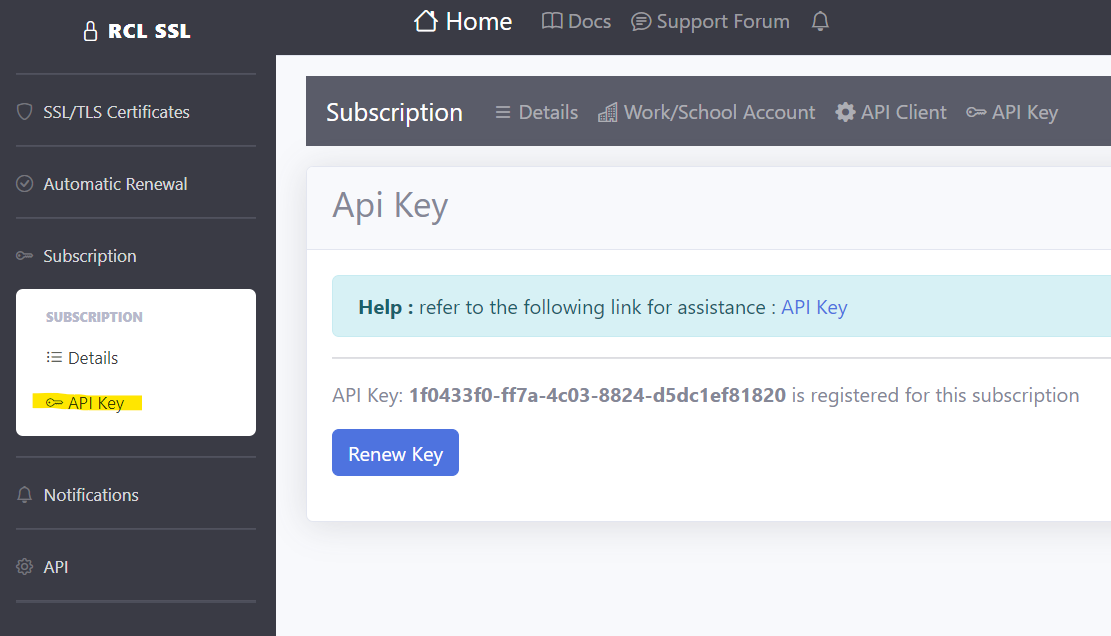
You will use the Api Key to obtain authorized access to API resources.
Get the Api Key
-
In the RCL SSL Portal side menu, click on Subscription > API Key
-
In the
API Keypage, you can view the API Key
V8.0
You will use the Api Key to obtain authorized access to API resources.
In the RCL SSL Portal side menu, click on Subscription > API Key
In the API Key page, you can view the API Key
