SAN Certificate - Azure Key Vault
V8.0
RCL SSL creates TLS/SSL certificates using an Azure DNS Zone and automatically saves them to Azure Key Vault.
A Subject Alternative Name (SAN) TLS/SSL certificate will contain multiple domains in a single certificate. SAN certificates created with an Azure DNS Zone will contain the domain (e.g. contoso.com) and the wild card domain (e.g. *.contoso.com) in a single TLS/SSL certificate.
Single Domains
SAN certificates only allow a single domain. For instance, the two domains ‘fabricam.com’ and ‘contoso.com’ are not allowed in a SAN multi-domain certificate.
Access Control
Organization Accounts
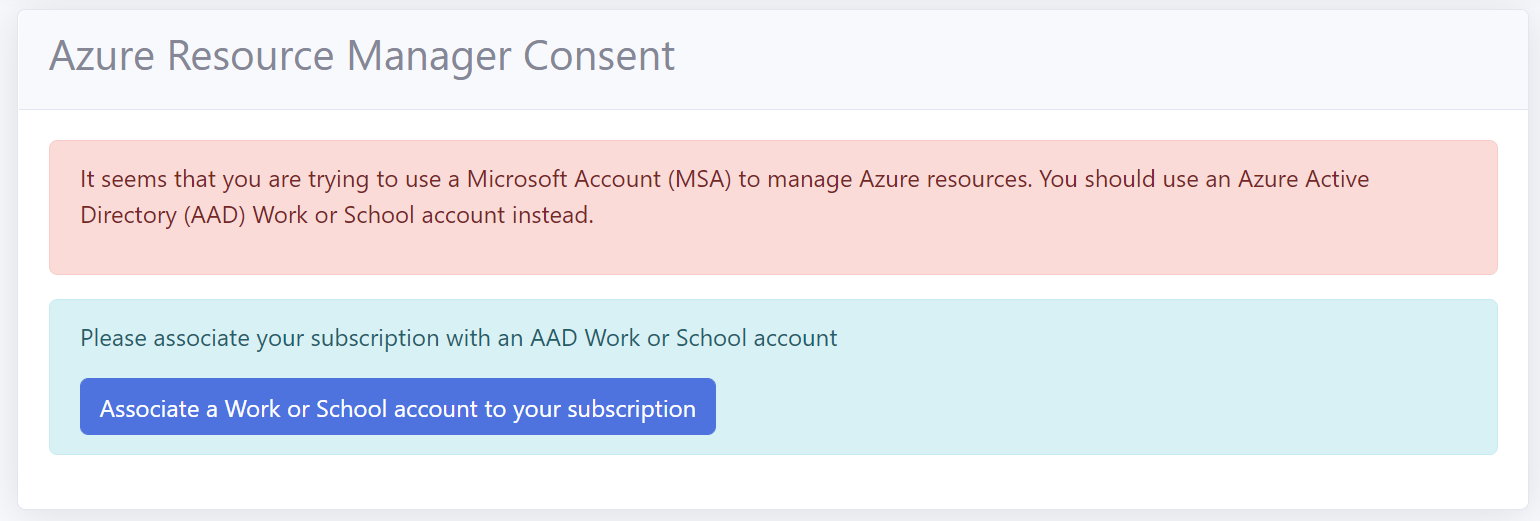
Personal Microsoft Accounts (MSA) are not supported for Azure resources in a subscription. Only Microsoft Entra ID (formerly AAD) organizational accounts (also known as ‘Work or School Accounts’) are supported.
If you try to manage an Azure DNS / Key Vault with a MSA account you will get the following error.
If you signed up for the RCL SSL Portal with a personal Microsoft account (MSA), please follow the instructions in the following link to associate an organization account to your RCL SSL subscription:
Set Access Control
To create certificates for Azure DNS / Key Vault, the Azure organizational account that you use to login to RCL SSL Portal must either be :
- Have a role of ‘Owner’ or ‘Contributor’ to the subscription containing the Azure DNS Zone(s) / Key Vault(s)
If either of these requirements are not met, the ‘Subscriptions’, ‘Key Vault’ and ‘DNS Zone’ lists will be empty when you try to create a certificate.
You may also experience an error message.
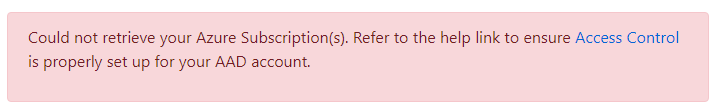
To set up access control for your organization account, follow the instructions in the link below :
Create a SSL/TLS Certificate using DNS-01
RCL SSL uses the DNS-01 challenge type to issue certificates for :
- primary domains (e.g. contoso.net)
- subdomains (e.g. store.contoso.net)
- wild card subdomains (e.g. *.contoso.net)
The DNS challenge type ONLY works with an Azure DNS Zone.
Create a DNS Zone and Configure Name Server
If you bought your domain with a domain registrar, you must set up your Azure DNS Zone to manage the records for your domain.
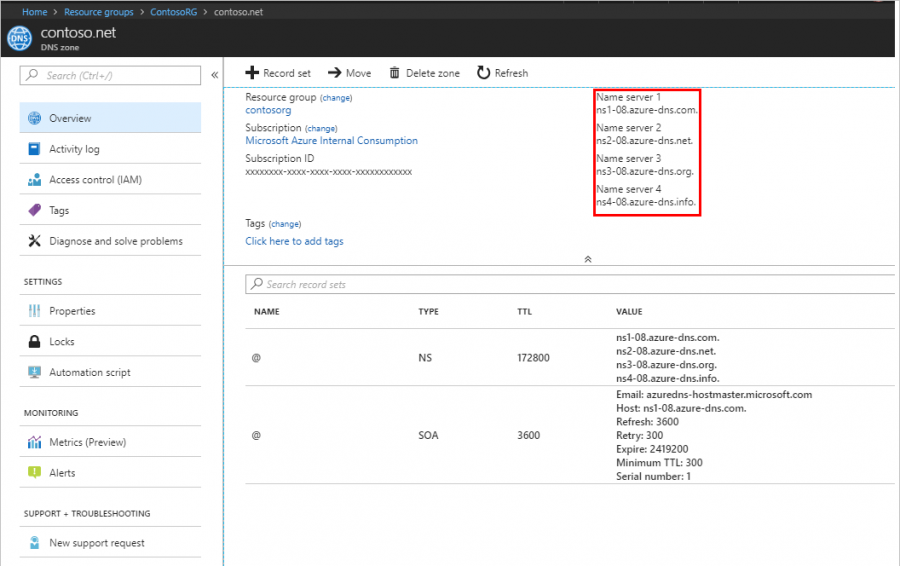
Follow the instructions in the link below to set up your Azure DNS Zone and delegate the name server (NS) records for your domain :
Azure Key Vault
If you do not have an Azure Key Vault, follow the steps in this link to create one :
Set Access Policy for Key Vault
If you do not set the access policy for Key Vault, you will experience ‘Access Denied’ or ‘Forbidden’ errors when you try to create a certificate.
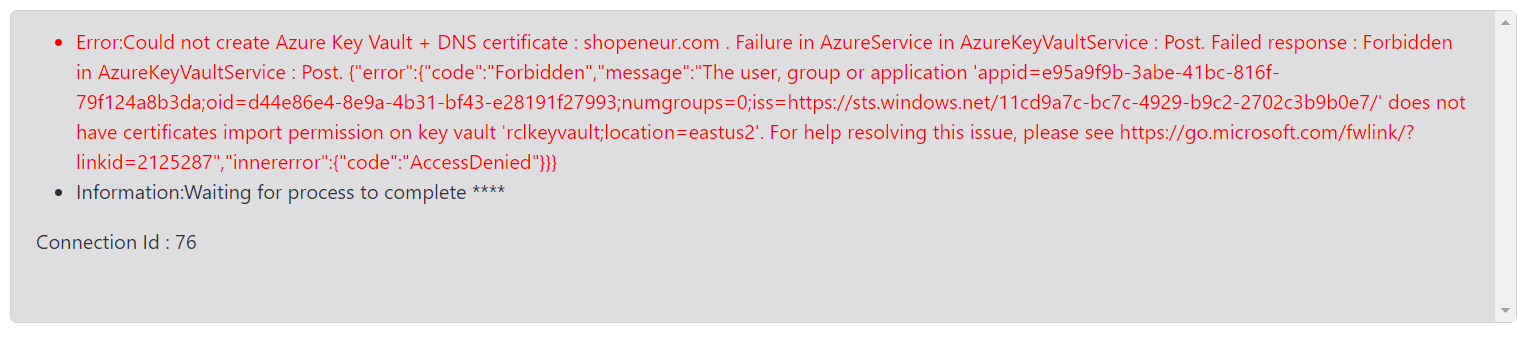
This access policy is required to import the SSL/TLS certificate in a Key Vault in your Azure account. If you have not yet created an access policy for your certificates, then follow these steps.
- In your Azure Key Vault, click on the ‘Access policies’ link. Then click on ‘Create’.
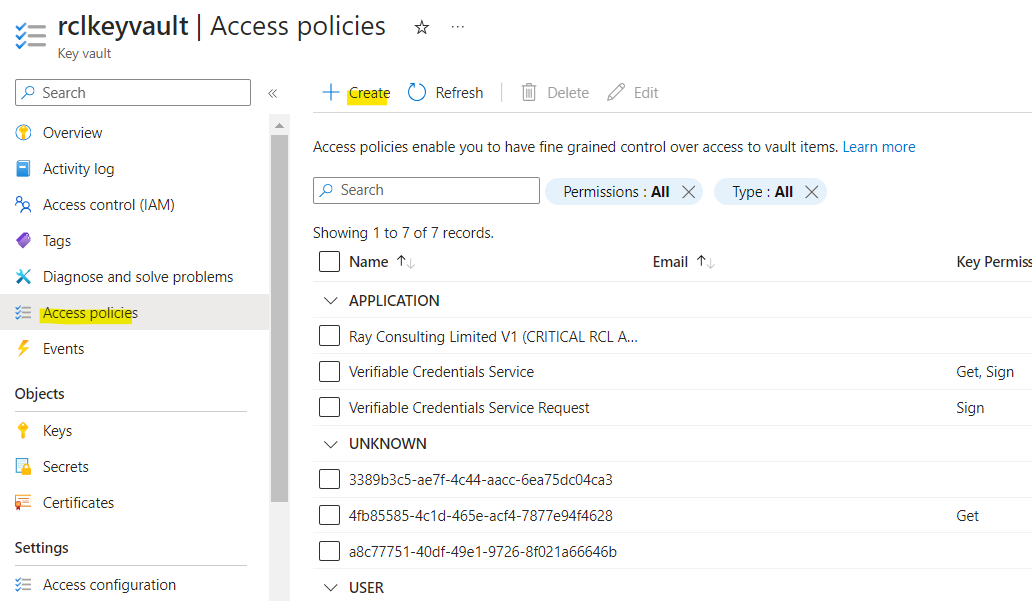
-
Select all the permissions for the ‘Certificate Management Operations’ (select all). Ensure you include the purge permission.
-
Select all the permissions for the ‘Secret Management Operations’ (select all). Ensure you include the purge permission.
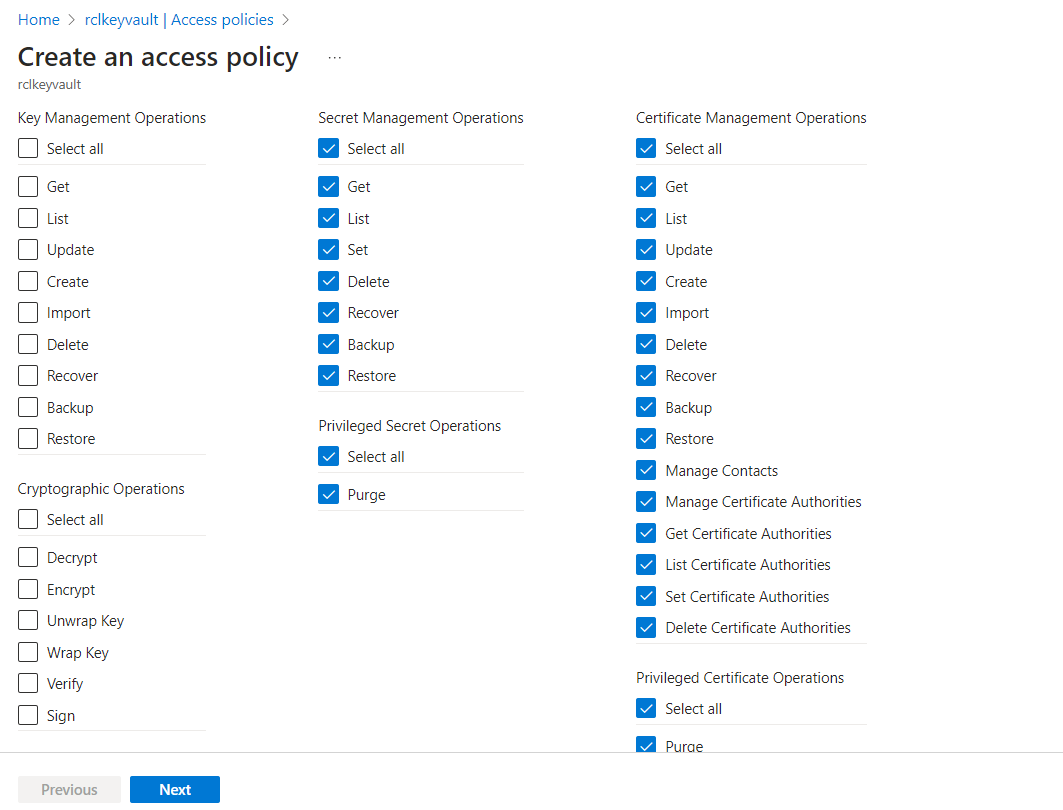
-
Click the ‘Next’ button when you are done
-
Select a service principal : search for the Azure Active Directory organizational user account that you use to login to the RCL SSL portal
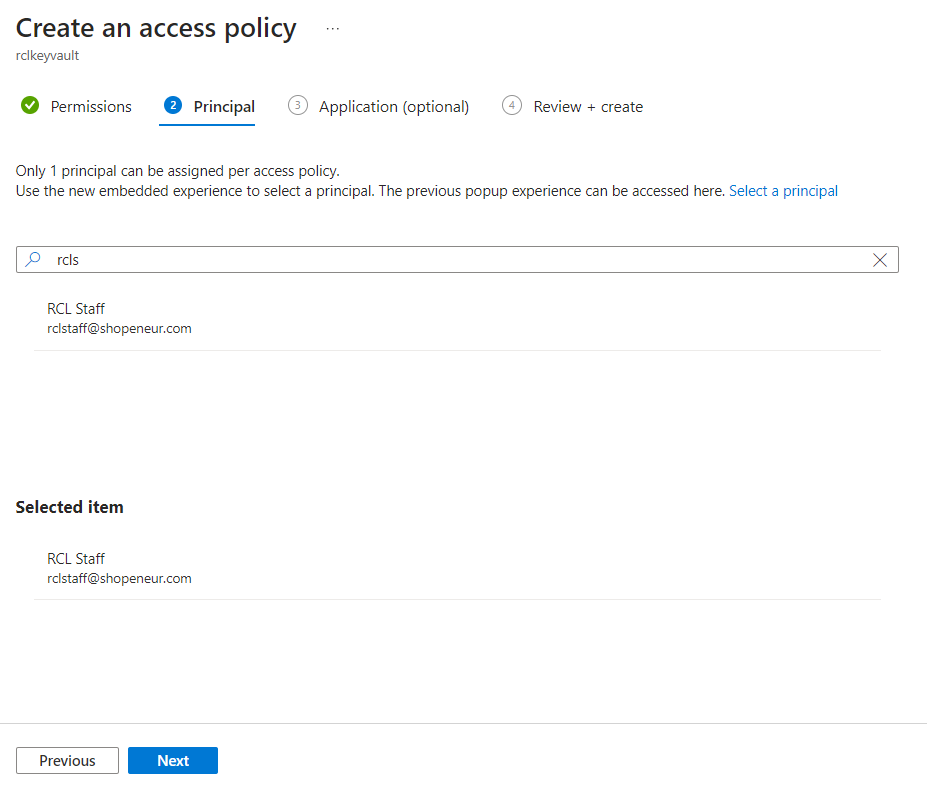
-
Click the ‘Next’ button
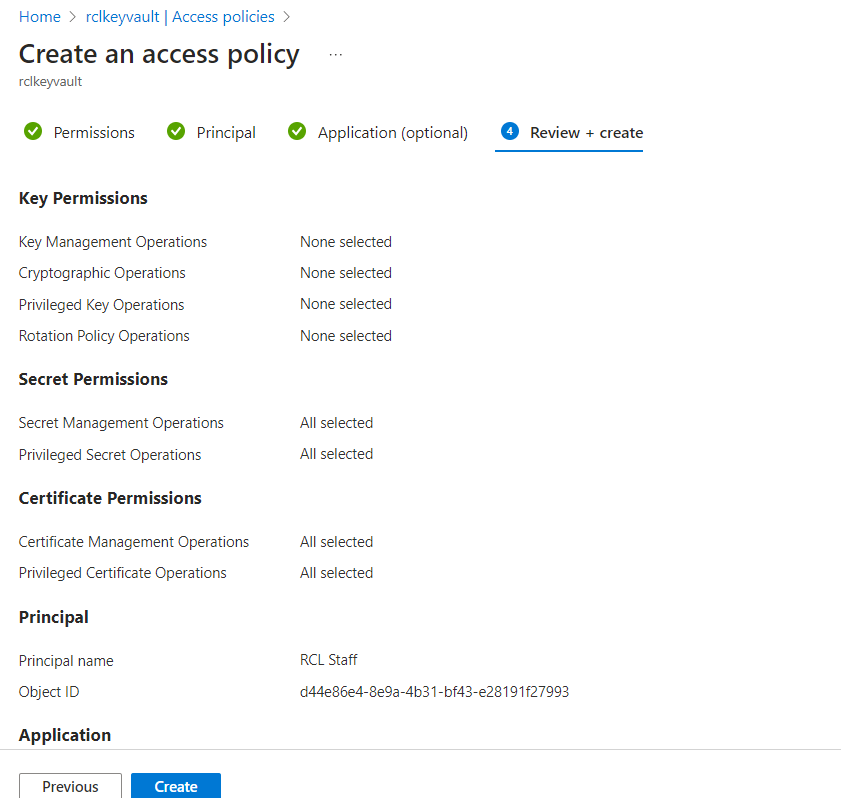
-
Click the ‘Create’ button when you are done
- The new access policy will be added
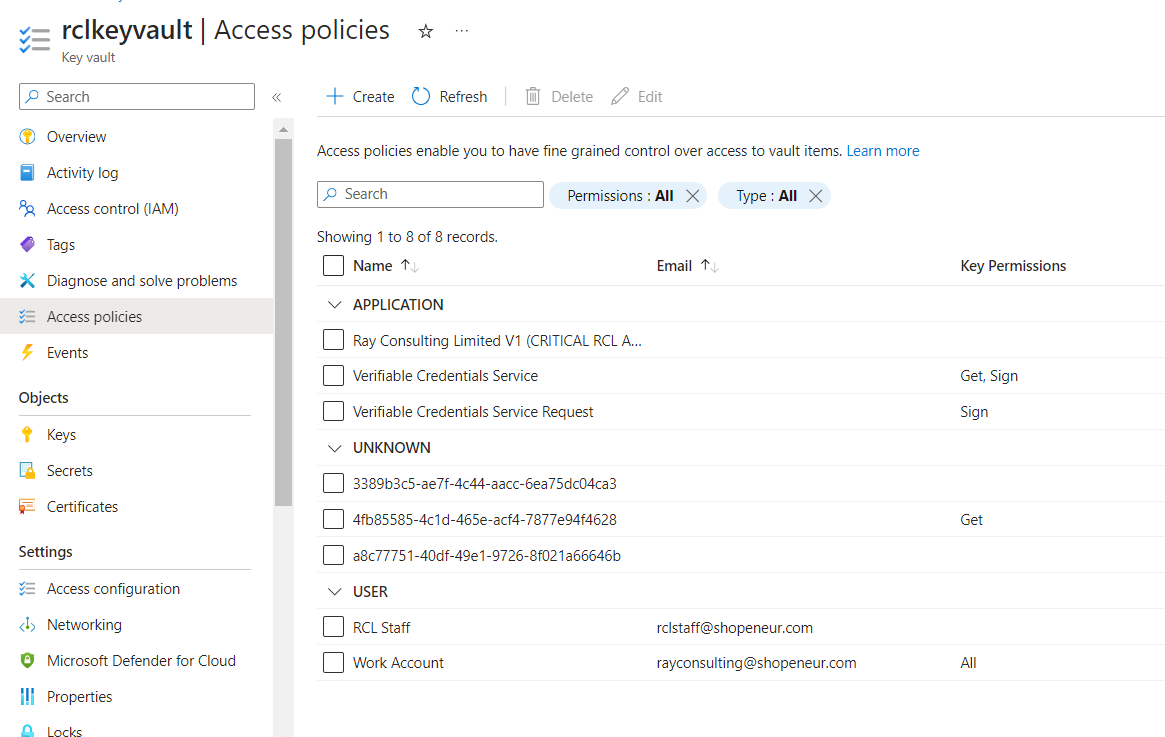
Create the SSL/TLS Certificate
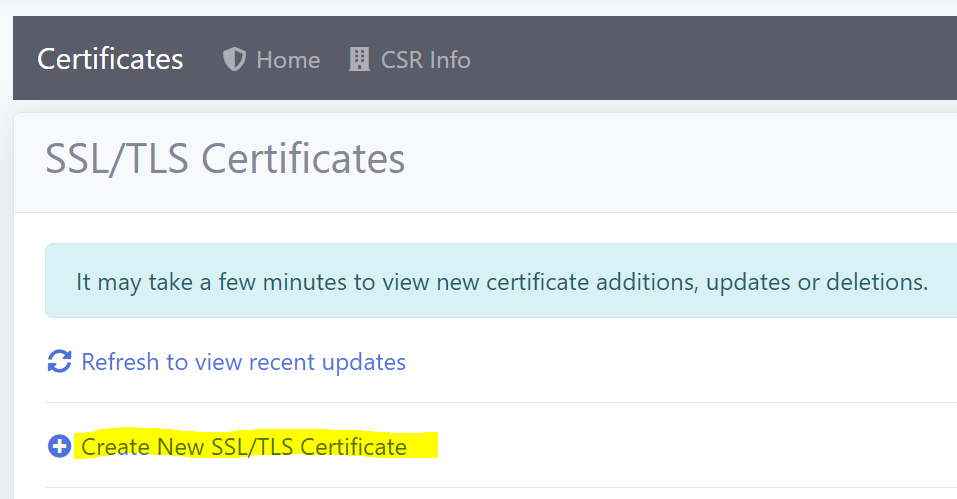
- In the ‘Certificates’ module of the portal, click on the Create New SSL/TLS Certificate link
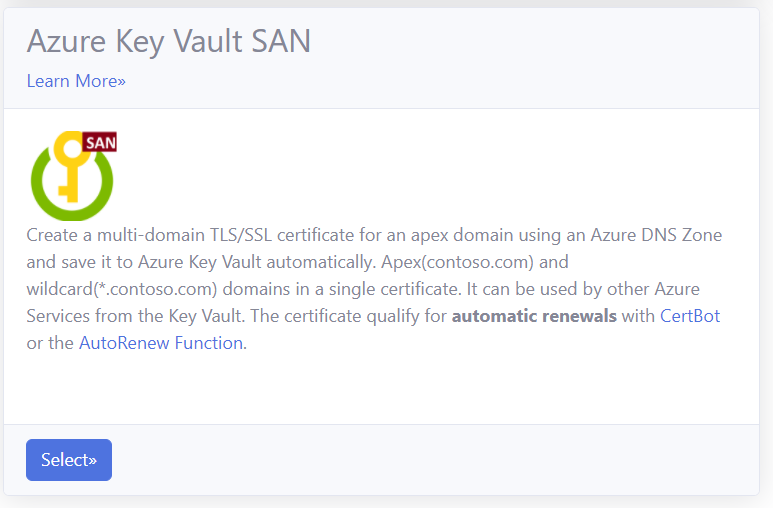
- Select the ‘Azure Key Vault SAN’ option.
-
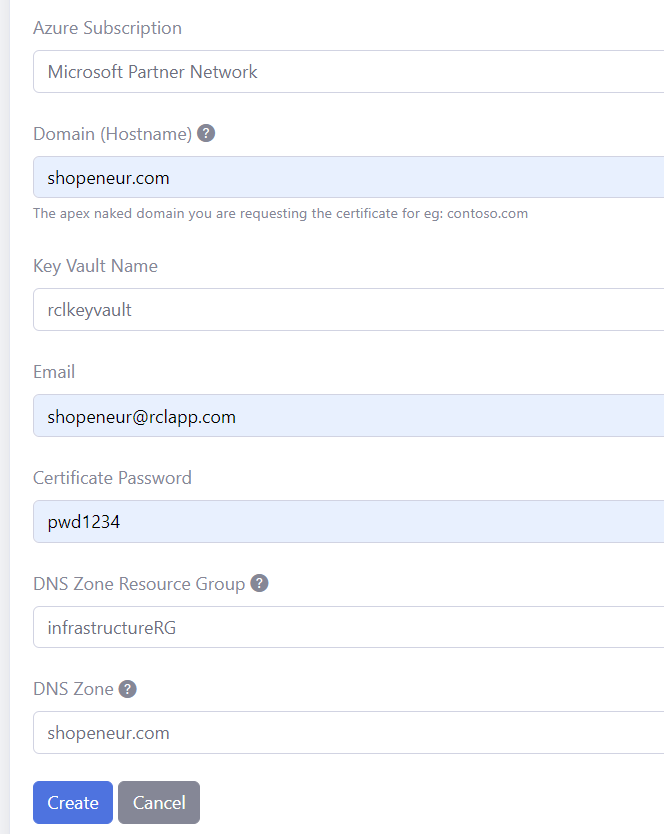
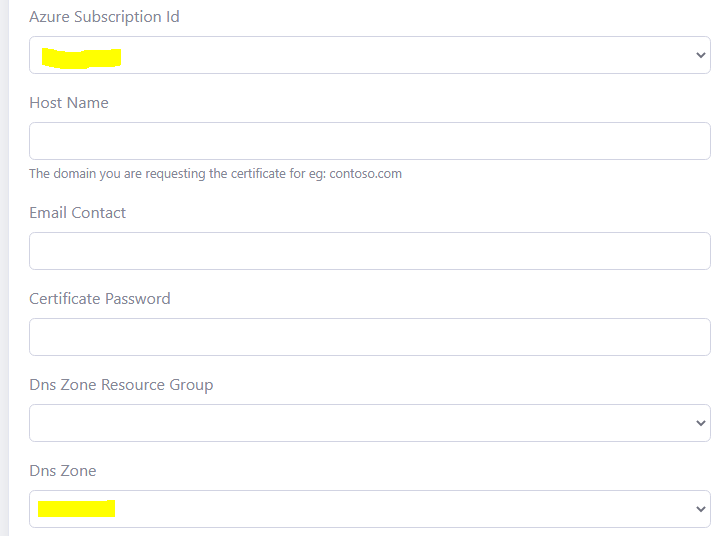
Add the data to create the certificate. The image below illustrates sample data.
-
The Hostname is the single Domain (eg: ‘contoso.com’) you are requesting the certificate for. Only a single domain is allowed. The additional wildcard domain (eg: *.contoso.com) will be automatically added to the certificate.
-
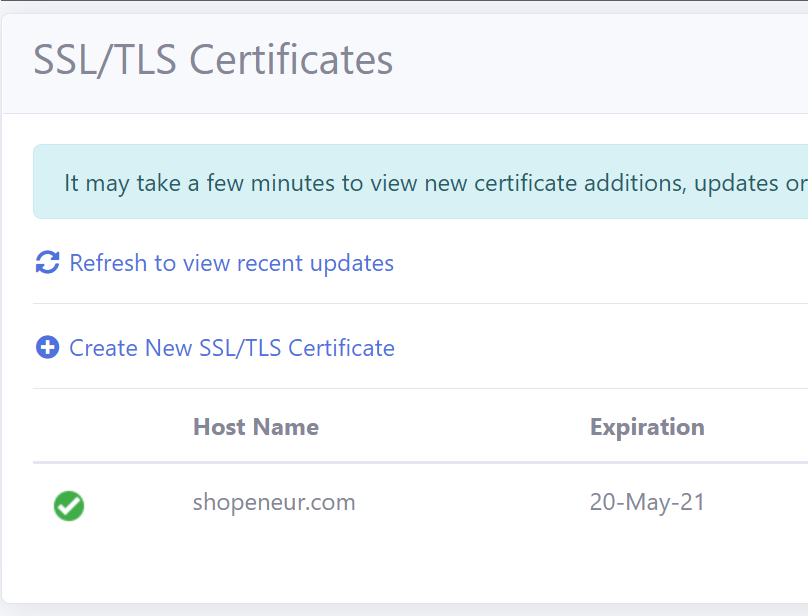
In the case above, we are requesting a SAN SSL/TLS certificate for the domain, ‘shopeneur.com’. The wild card domain ‘*.shopeneur.com’ will be automatically included in the certificate.
-
Select the Key Vault name.
-
The Host Name must be valid for the DNS Zone. For instance, the domain ‘shopeneur.com’ is valid for the DNS Zone ‘shopeneur.com’
-
Click the Create Button when you are done
-
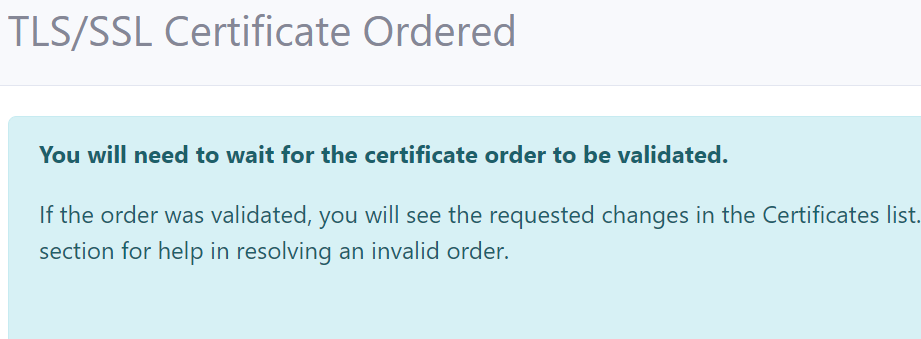
You will need to wait up to 10 mins to validate the site and install the certificate. When this is done, the SSL/TLS certificate will be displayed in the certificates list.
- When this is done, the TLS/SSL certificate will be displayed in the certificates list.
- You can now access your certificate in your Azure Key Vault in the Azure portal.
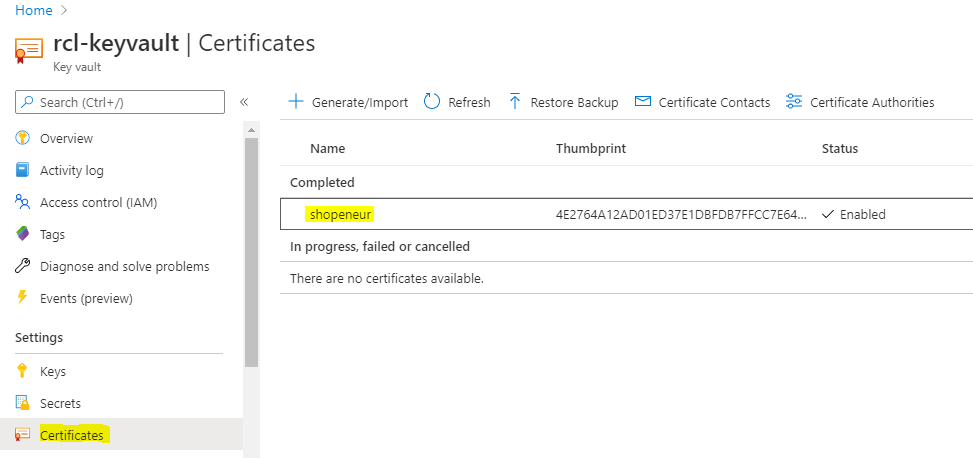
Manually Renewing TLS/SSL Certificates
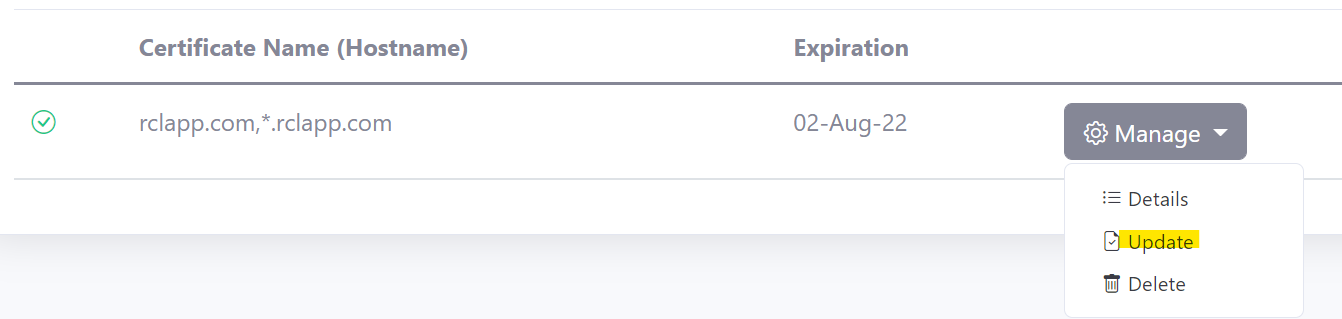
SSL/TLS certificates will expire in 90 days. You can manually renew a certificate at any point before the expiry date. Click on the ‘Renew’ link in the ‘Manage’ menu in the certificates list to update a certificate.
Automatic Certificate Renewal and Installation
You can use the RCL SSL AutoRenew Function to automatically renew certificates in Azure Key Vault.
Follow the instructions in the link to use the AutoRenew function :
Azure Key Vault with Application Gateway
You can use Azure Key Vault certificates with an Azure Application Gateway.
Azure Key Vault with Azure Kubernetes Service
You can use Azure Key Vault certificates with Azure Kubernetes Service.
Rate Limits
There is a rate limit of 50 SSL/TLS certificates per subscription.
In addition, Let’s Encrypt has instituted rate limits to ensure fair usage by as many people as possible. To find out more about these rate limits please refer to the following link :